
In today’s rapidly evolving digital world, cyber security remains a paramount concern for businesses globally, with Kenya being no exception. As the country advances technologically, the imperative for companies of all sizes to recognize and address cyber security challenges has never been more critical.
Our exclusive conversation with Erick Njoroge, a Security Engineer at Check Point, offers a deep dive into Kenya’s cyber security landscape, highlighting the urgent need for businesses to bolster their cyber security frameworks in this digital age.
Overview of Check Point
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leader in AI-powered, cloud-delivered cyber security, safeguarding over 100,000 organizations worldwide. The company leverages AI across its Infinity Platform to boost cyber security efficiency and precision, featuring industry-leading detection rates that foster proactive threat identification and expedited response efforts.
Check Point provides an extensive array of cyber security solutions for a global clientele, spanning network, endpoint, cloud, mobile, and data security, alongside security management.
Founded in 1993 by Gil Shwed, who plans to transition from CEO to an ‘active’ executive chair role this year, Check Point introduced the world to stateful inspection technology. This was the cornerstone of their inaugural product, FireWall-1, leading to the development of VPN-1, the first in a lineage of VPN products.
Embracing Fifth Generation Cyber Security
Check Point’s commitment to “fifth generation cyber security” is evident in their strategy to safeguard all networks, cloud services, and mobile platforms against advanced threats that traditional, static defenses often fail to counter.
Solutions Provided by Check Point
The company’s product suite is vast, addressing various cyber security needs:
- Infinity Platform: Integrates Infinity Core Services and Infinity Portal Access, offering unified protection.
- Network Security: Features like Next Generation Firewalls (NGFW) and SD-WAN.
- Cloud Security: CloudGuard and other tools ensure cloud environments are secure.
- Workspace Security: Harmony, Endpoint Security, and Mobile Security guard against threats to user devices and data.
- Security Operations and AI: Services such as Managed Prevention & Response, along with Infinity AI Copilot, automate and optimize security operations.
Cyber Security in Kenya: Challenges and Check Point’s Response
Kenya’s cyber security landscape is challenging, with organizations facing an average of 2,198 attacks per week, significantly higher than the global average of 1,058 attacks. The August DDOS attack on Kenya’s eCitizen portal, attributed to Anonymous Sudan, underscores these challenges.
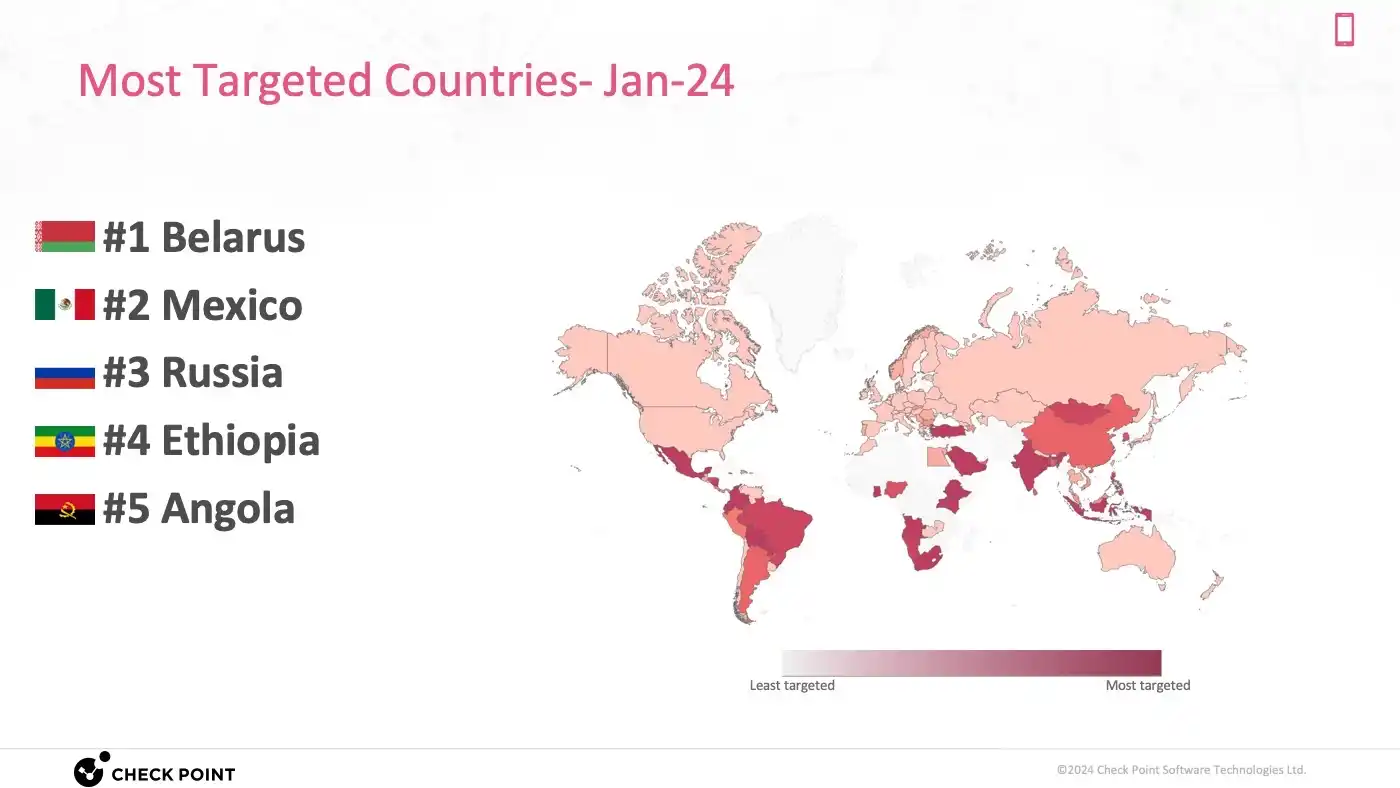
Check Point’s holistic cyber security approach, emphasizing network, office, device, and personnel security, alongside the deployment of Infinity AI Copilot, showcases their commitment to addressing these threats with advanced AI and cloud technologies.
When discussing the state of cyber security in kenya, Mr. Njoroge said Kenya is a country that has and still supports innovation and technology. This is a net positive but there are risks associated with technological advancements. He said one of the biggest issues when it comes to cyber security for enterprises is with organizations running legacy platforms. Most of these platforms do not meet the current standards and can be a huge risk for organizations.
Another issue is with organizations acquiring new technology without the technical know-how or even having the right number of professionals or manpower to handle it. Mr. Njoroge states that, “In cyber security, people are the weakest link in an organization.” With this in mind, there is a need to provide enough skills and training to individuals in organizations.
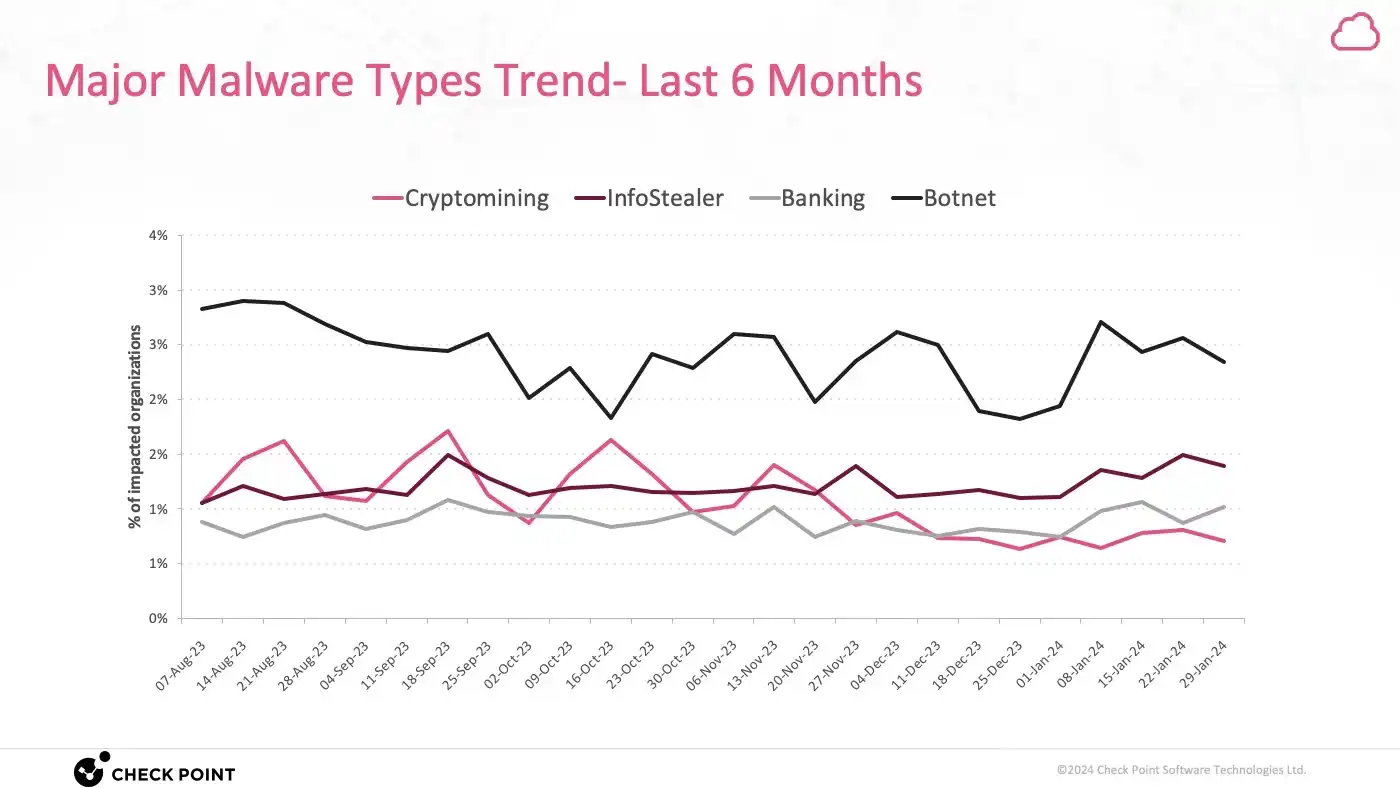
Organizations also need better policies and processes beyond the technology they acquire. Having the best products to defend against cyber security attacks is important to ensure there are policies that are geared towards ensuring the smooth running of the technology. For example, if an organization gives its employees laptops to use for work, are there guidelines that ensure these devices are used for what they are intended to? This is just one way to approach this to make sure everyone in the organization is on the same page.
AI in Cyber Security
The integration of AI in cyber security has transformed defense capabilities and threat creation alike. Check Point’s introduction of Infinity AI Copilot exemplifies the potential of AI to revolutionize cyber security practices by automating complex tasks and proactively addressing security threats.
Initiating Cyber Security Measures
For businesses embarking on their cyber security journey, Check Point recommends:
- Comprehensive environmental understanding.
- In-depth assessments to identify and analyze risks.
- Simplification and consolidation for enhanced visibility and control.
- A layered security strategy.
- Adoption of least privilege principles.
- Technology embracement, including AI and cloud solutions, for improved security.
Through Erick Njoroge’s insights, the critical need for robust cybersecurity measures in Kenya is evident. Check Point’s advanced solutions, particularly their innovative use of AI and cloud technologies, provide a model for organizations aiming to strengthen their cybersecurity defenses against the backdrop of evolving digital threats.
Also Read: Kenya’s mobile-first strategies make fintechs vulnerable to cyber attacks

